The general trend towards Industrial IoT, Industry 4.0 and connecting OT (operations technology) to IT faces a serious challenge: security. Acquiring process data is becoming essential to stay competitive, but most plant engineers and supervisors are wary of exposing their OT systems to the outside world. And who can blame them as ransomware and infrastructure attacks skyrocket?
The best way to secure industrial systems, according to industry experts and government agencies alike, is to segregate OT and IT networks using a DMZ (demilitarized zone).
A DMZ isolates the production system from IT, ensuring no direct link between corporate networks and control networks. Only known and authenticated actors can enter the system at all. Firewalls can protect both operations and IT sides and should be configured to allow only outbound connections to the DMZ. This ensures that only the correct data passes between networks.
Challenges for OPC UA and MQTT
However, implementing a DMZ in an Industrial IoT environment is problematic for the two most used IoT protocols: OPC UA and MQTT. Getting data out of a plant through a DMZ typically requires two or more servers, chained together one after the other.
The OPC UA protocol is simply too complex to reproduce well in a daisy chain like this. Information will be lost in the first hop. The synchronous multi-hop interactions needed to pass data across a DMZ would be fragile on all but the most reliable networks and would result in high latencies. Also, there would be no access to the data at each node in the chain.
MQTT, on the other hand, can be chained but it requires each node in the chain to be aware that it is part of the chain and to be individually configured. The QoS (quality of service) guarantees in MQTT cannot propagate through the chain, making data at the ends of the chain unreliable.
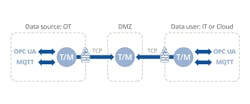
A tunnel/mirror solution
Since neither OPC UA nor MQTT is well-suited to passing data through a DMZ, another approach is needed—one that integrates well with both protocols. Secure tunnel/mirroring software can do this and pass the data along daisy-chained connections, securely crossing a DMZ.
The tunnel/mirror software (T/M in the accompanying illustration) connects to either MQTT or OPC UA at each end of the tunnel and mirrors the full data set through each server in the chain. It maintains the data in a unified namespace and provides access to it for registered, qualified clients at each node as well as at the final destination. The mirroring capability of the tunnel/mirroring software guarantees consistency so that any client or intermediate point in the chain remains consistent with the original data source.
Access to operations data is becoming essential in today’s competitive environment—and there is no reason such access cannot be secure. It is possible to fully segregate OT and IT networks and still allow qualified users to access your production data. Segregating networks using a DMZ is the recommended approach, and this is best implemented with secure tunnel/mirroring.
Xavier Mesrobian is vice president of sales and marketing at Skkynet Cloud Systems Inc.